Targeted Tech Talk Video Channel on YouTube
Targeted Tech Talk Video Channel on Bitchute
Targeted Tech Talk Video Channel on Rumble
Episode 10 – LoRa Radio Demo – Published December 6, 2025

Episode 9 – GPS Satellite Tracker – Published October 25, 2025

Episode 8 – Types of Cyber Threats – Published October 14, 2025

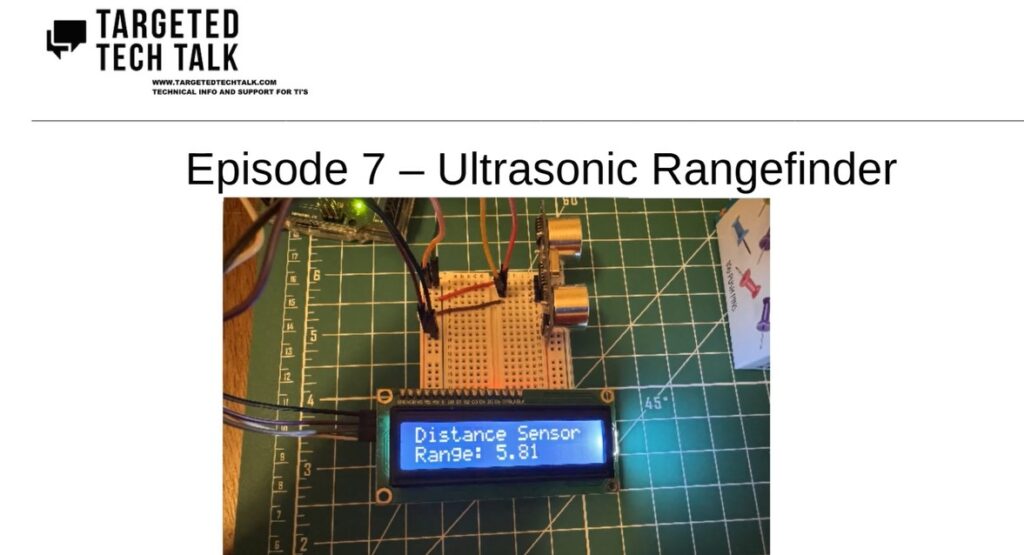
Episode 7 – Ultrasonic Rangefinder – Published September 21, 2025
Episode 6 – GhostTouch – Published September 1, 2025

Episode 5 – Secure Computing Basics – Published August 17, 2025

Episode 4 – Tor vs VPN – Published August 6, 2025

Episode 3 – ESP32 Marauder Demo – Published July 29, 2025

Episode 2 – ESP32 Marauder Build – Published July 20, 2025

Episode 1 – File Hashing / File Checksum Verification Demo Video – Published July 13, 2025

Website Overview Video – Published July 4, 2025

I was the guest speaker on Targeted West Show #151 2/9/25
Rumble – https://t.co/geFzYByRp7
YouTube – https://t.co/ajcOdZKawO





